Cyber Threats and Solutions in the Supply Chain with Joe Ohr
The Logistics of Logistics
AUGUST 29, 2024
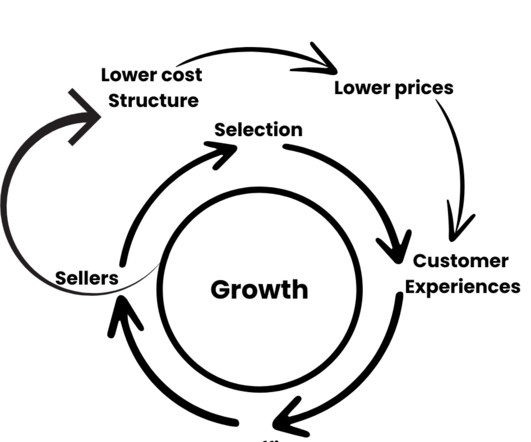
With extensive connectivity across multi-tier supplier networks, stringent authentication, encryption, and zero-trust models are crucial for secure data sharing and mitigating vulnerabilities. The rise of cargo theft through cybersecurity loopholes demands robust countermeasures like two-factor authentication and restricted access controls.




































Let's personalize your content